Back door attacks utilize programs that provide a mechanism for entering a system without going through the usual authentication process. This can either take the form of hidden access points intentionally put into an application by the original developers to aid in maintaining and debugging the software which were then left in when the software was installed by customers, or a malicious program that is placed on a system via a virus or other method which opens up the system to unauthorized access.
Back Door Attacks: Back Orifice, NetBus and Sub7
A number of back door programs have been discovered over the years which can be used in back door attacks. Here are some of them:
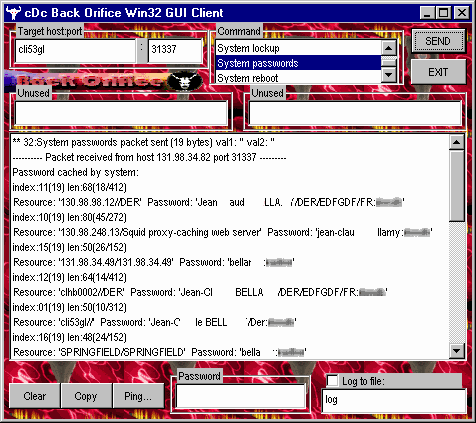
- Back Orifice: The brainchild of Sir Dystic of Cult of the Dead Cow, its initial purpose was to show the lack of security in Windows 98 (it was released in 1998), Back Orifice has legitimate purposes, such as remote administration. But it also has attributes that make it suited for less benign uses such as back door attacks. The server can hide itself from cursory looks by users of the system. As the server can be installed without user interaction, it can be distributed as the payload of a Trojan horse. As a result, the antivirus industry immediately categorized the tool as malware and appended Back Orifice to their quarantine lists. Two sequel applications followed: Back Orifice 2000 (released in 1999), and Deep Back Orifice by French Canadian hacking group QHA.
- NetBus: Another program that can be used in back door attacks, this is a software program for remotely controlling a Microsoft Windows computer system over a network. It was released in 1998, a few months before Back Orifice. There are two components to the client-server architecture. The server must be installed and run on the computer that should be remotely controlled. The server was an .EXE file with a size of about 500 KB. When started for the first time, the server would install itself on the host computer, including modifying the Windows registry so that i starts automatically on each system startup. The server is a faceless process listening for connections on port 12345, with the port number adjustable on later versions. the client was a separate program presenting a graphical user interface that allowed the user to perform a number of activities on the remote computer, such as keystroke logging, screen captures, file browsing, opening and closing the CD-tray, and using tunneling protocols. The NetBus client was designed work under Windows 95/98/ME/NT 4.0, as well as Windows 2000/XP. Major parts of the protocol are textual, and as a result, the server can be controlled by typing commands over a raw TCP connection from a non-Windows computer.
- Sub7: Originally designed by someone with the handle “mobman”, the name “Sub7″ was derived by spelling “NetBus” backwards (“SubTen”) and swapping “ten” with “seven”. Because its typical use is to allow undetected and unauthorized access, Sub7 is usually described as a trojan horse by security experts. Like Back Orifice and NetBus, Sub7 is distributed with a server and a client. Sub7 has more features than NetBus, such as webcam capture, multiple port redirect, a user-friendly registry editor and chat, as well as penetration testing features, including a port scanner and a port redirector. Customizations possible with the Sub7 server editor included changing the port addresses, displaying a customized message upon installation. If the intent of the person deploying Sub7 is to launch a back door attack on a system, then the customized message can be used to deceive the victim and mask the true intent of the program. Nearly all antivirus programs can detect Sub7 and prevent it from being installed unless steps are taken to hide it.
Although the installation of any of the above mentioned back door programs will compromise network security, all of these threats can be prevented effectively by implementing a comprehensive virus scanning strategy.
External Links:
The post Back Door Attacks appeared first on pfSense Setup HQ.